Appendix A to Subpart A of Part 248 - Forms
17:4.0.1.1.9.1.128.22.1 : Appendix A
Appendix A to Subpart A of Part 248 - Forms
A. Any person may view and print this form at:
http://www.sec.gov/about/forms/secforms.htm.
B. Use of Form S-P by brokers, dealers, and investment
companies, and investment advisers registered with the Commission
constitutes compliance with the notice content requirements of §§
248.6 and 248.7 of this part.
FORM S-P - Model Privacy Form A. The Model Privacy Form
B. General
Instructions 1. How the Model Privacy Form is Used
(a) The model form may be used, at the option of a financial
institution, including a group of financial institutions that use a
common privacy notice, to meet the content requirements of the
privacy notice and opt-out notice set forth in §§ 248.6 and 248.7
of this part.
(b) The model form is a standardized form, including page
layout, content, format, style, pagination, and shading.
Institutions seeking to obtain the safe harbor through use of the
model form may modify it only as described in these
instructions.
(c) Note that disclosure of certain information, such as assets,
income, and information from a consumer reporting agency, may give
rise to obligations under the Fair Credit Reporting Act [15 U.S.C.
1681-1681x] (FCRA), such as a requirement to permit a consumer to
opt out of disclosures to affiliates or designation as a consumer
reporting agency if disclosures are made to nonaffiliated third
parties.
(d) The word “customer” may be replaced by the word “member”
whenever it appears in the model form, as appropriate.
2. The Contents of the Model Privacy Form
The model form consists of two pages, which may be printed on
both sides of a single sheet of paper, or may appear on two
separate pages. Where an institution provides a long list of
institutions at the end of the model form in accordance with
Instruction C.3(a)(1), or provides additional information in
accordance with Instruction C.3(c), and such list or additional
information exceeds the space available on page two of the model
form, such list or additional information may extend to a third
page.
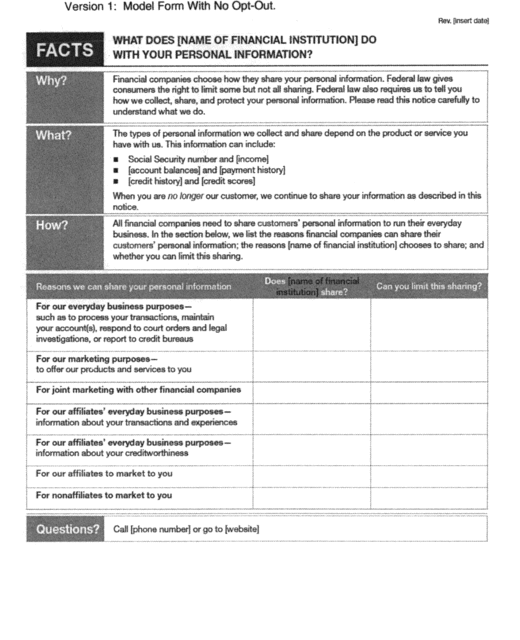
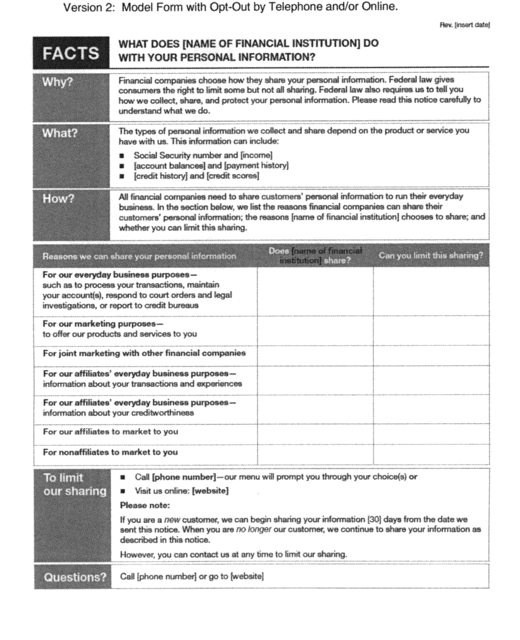
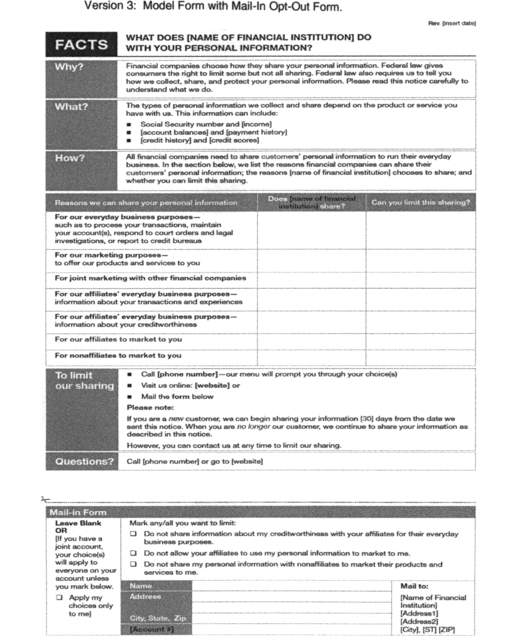
(a) Page One. The first page consists of the following
components:
(1) Date last revised (upper right-hand corner).
(2) Title.
(3) Key frame (Why?, What?, How?).
(4) Disclosure table (“Reasons we can share your personal
information”).
(5) “To limit our sharing” box, as needed, for the financial
institution's opt-out information.
(6) “Questions” box, for customer service contact
information.
(7) Mail-in opt-out form, as needed.
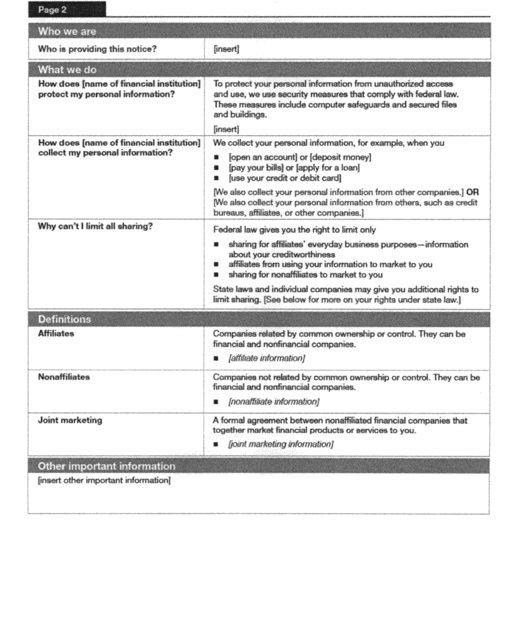
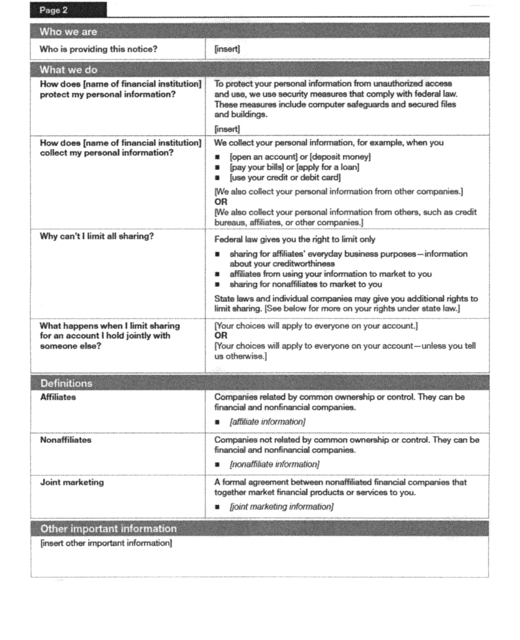
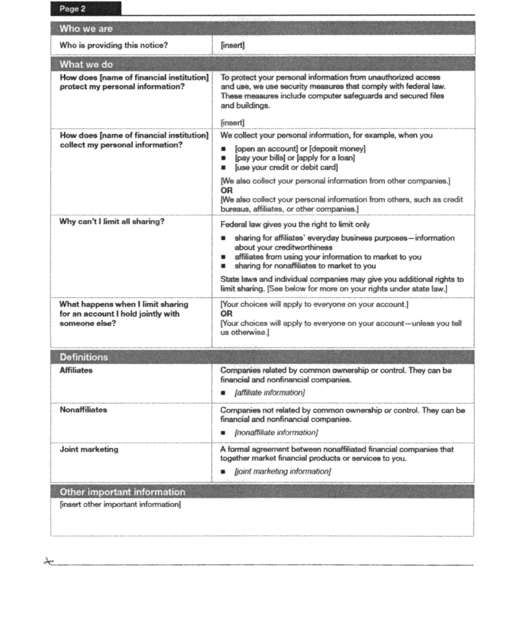
(b) Page Two. The second page consists of the following
components:
(1) Heading (Page 2).
(2) Frequently Asked Questions (“Who we are” and “What we
do”).
(3) Definitions.
(4) “Other important information” box, as needed.
3. The Format of the Model Privacy Form
The format of the model form may be modified only as described
below.
(a) Easily readable type font. Financial institutions
that use the model form must use an easily readable type font.
While a number of factors together produce easily readable type
font, institutions are required to use a minimum of 10-point font
(unless otherwise expressly permitted in these Instructions) and
sufficient spacing between the lines of type.
(b) Logo. A financial institution may include a corporate
logo on any page of the notice, so long as it does not interfere
with the readability of the model form or the space constraints of
each page.
(c) Page size and orientation. Each page of the model
form must be printed on paper in portrait orientation, the size of
which must be sufficient to meet the layout and minimum font size
requirements, with sufficient white space on the top, bottom, and
sides of the content.
(d) Color. The model form must be printed on white or
light color paper (such as cream) with black or other contrasting
ink color. Spot color may be used to achieve visual interest, so
long as the color contrast is distinctive and the color does not
detract from the readability of the model form. Logos may also be
printed in color.
(e) Languages. The model form may be translated into
languages other than English.
C. Information Required in the Model Privacy Form
The information in the model form may be modified only as
described below:
1. Name of the Institution or Group of Affiliated Institutions
Providing the Notice
Insert the name of the financial institution providing the
notice or a common identity of affiliated institutions jointly
providing the notice on the form wherever [name of financial
institution] appears.
2. Page One
(a) Last revised date. The financial institution must
insert in the upper right-hand corner the date on which the notice
was last revised. The information shall appear in minimum 8-point
font as “rev. [month/year]” using either the name or number of the
month, such as “rev. July 2009” or “rev. 7/09”.
(b) General instructions for the “What?” box. (1) The
bulleted list identifies the types of personal information that the
institution collects and shares. All institutions must use the term
“Social Security number” in the first bullet.
(2) Institutions must use five (5) of the following terms to
complete the bulleted list: income; account balances; payment
history; transaction history; transaction or loss history; credit
history; credit scores; assets; investment experience; credit-based
insurance scores; insurance claim history; medical information;
overdraft history; purchase history; account transactions; risk
tolerance; medical-related debts; credit card or other debt;
mortgage rates and payments; retirement assets; checking account
information; employment information; wire transfer
instructions.
(c) General instructions for the disclosure table. The
left column lists reasons for sharing or using personal
information. Each reason correlates to a specific legal provision
described in paragraph C.2(d) of this Instruction. In the middle
column, each institution must provide a “Yes” or “No” response that
accurately reflects its information sharing policies and practices
with respect to the reason listed on the left. In the right column,
each institution must provide in each box one of the following
three (3) responses, as applicable, that reflects whether a
consumer can limit such sharing: “Yes” if it is required to or
voluntarily provides an opt-out; “No” if it does not provide an
opt-out; or “We don't share” if it answers “No” in the middle
column. Only the sixth row (“For our affiliates to market to you”)
may be omitted at the option of the institution. See
paragraph C.2(d)(6) of this Instruction.
(d) Specific disclosures and corresponding legal
provisions. (1) For our everyday business purposes. This
reason incorporates sharing information under §§ 248.14 and 248.15
and with service providers pursuant to § 248.13 of this part other
than the purposes specified in paragraphs C.2(d)(2) or C.2(d)(3) of
these Instructions.
(2) For our marketing purposes. This reason incorporates
sharing information with service providers by an institution for
its own marketing pursuant to § 248.13 of this part. An institution
that shares for this reason may choose to provide an opt-out.
(3) For joint marketing with other financial companies.
This reason incorporates sharing information under joint marketing
agreements between two or more financial institutions and with any
service provider used in connection with such agreements pursuant
to § 248.13 of this part. An institution that shares for this
reason may choose to provide an opt-out.
(4) For our affiliates' everyday business purposes -
information about transactions and experiences. This reason
incorporates sharing information specified in sections
603(d)(2)(A)(i) and (ii) of the FCRA. An institution that shares
for this reason may choose to provide an opt-out.
(5) For our affiliates' everyday business purposes -
information about creditworthiness. This reason incorporates
sharing information pursuant to section 603(d)(2)(A)(iii) of the
FCRA. An institution that shares for this reason must provide an
opt-out.
(6) For our affiliates to market to you. This reason
incorporates sharing information specified in section 624 of the
FCRA. This reason may be omitted from the disclosure table when:
the institution does not have affiliates (or does not disclose
personal information to its affiliates); the institution's
affiliates do not use personal information in a manner that
requires an opt-out; or the institution provides the affiliate
marketing notice separately. Institutions that include this reason
must provide an opt-out of indefinite duration. An institution that
is required to provide an affiliate marketing opt-out, but does not
include that opt-out in the model form under this part, must comply
with section 624 of the FCRA and 17 CFR part 248, subpart B, with
respect to the initial notice and opt-out and any subsequent
renewal notice and opt-out. An institution not required to provide
an opt-out under this subparagraph may elect to include this reason
in the model form.
(7) For nonaffiliates to market to you. This reason
incorporates sharing described in §§ 248.7 and 248.10(a) of this
part. An institution that shares personal information for this
reason must provide an opt-out.
(e) To limit our sharing: A financial institution must
include this section of the model form only if it provides
an opt-out. The word “choice” may be written in either the singular
or plural, as appropriate. Institutions must select one or more of
the applicable opt-out methods described: telephone, such as by a
toll-free number; a Web site; or use of a mail-in opt-out form.
Institutions may include the words “toll-free” before telephone, as
appropriate. An institution that allows consumers to opt out online
must provide either a specific Web address that takes consumers
directly to the opt-out page or a general Web address that provides
a clear and conspicuous direct link to the opt-out page. The
opt-out choices made available to the consumer who contacts the
institution through these methods must correspond accurately to the
“Yes” responses in the third column of the disclosure table. In the
part titled “Please note” institutions may insert a number that is
30 or greater in the space marked “[30].” Instructions on voluntary
or state privacy law opt-out information are in paragraph C.2(g)(5)
of these Instructions.
(f) Questions box. Customer service contact information
must be inserted as appropriate, where [phone number] or [Web site]
appear. Institutions may elect to provide either a phone number,
such as a toll-free number, or a Web address, or both. Institutions
may include the words “toll-free” before the telephone number, as
appropriate.
(g) Mail-in opt-out form. Financial institutions must
include this mail-in form only if they state in the “To
limit our sharing” box that consumers can opt out by mail. The
mail-in form must provide opt-out options that correspond
accurately to the “Yes” responses in the third column in the
disclosure table. Institutions that require customers to provide
only name and address may omit the section identified as “[account
#].” Institutions that require additional or different information,
such as a random opt-out number or a truncated account number, to
implement an opt-out election should modify the “[account #]”
reference accordingly. This includes institutions that require
customers with multiple accounts to identify each account to which
the opt-out should apply. An institution must enter its opt-out
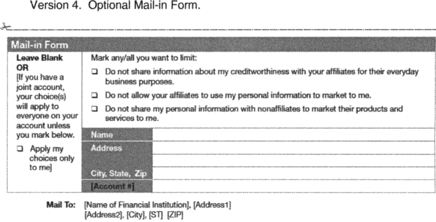
mailing address: in the far right of this form (see version
3); or below the form (see version 4). The reverse side of
the mail-in opt-out form must not include any content of the model
form.
(1) Joint accountholder. Only institutions that provide
their joint accountholders the choice to opt out for only one
accountholder, in accordance with paragraph C.3(a)(5) of these
Instructions, must include in the far left column of the mail-in
form the following statement: “If you have a joint account, your
choice(s) will apply to everyone on your account unless you mark
below. □ Apply my choice(s) only to me.” The word “choice” may be
written in either the singular or plural, as appropriate. Financial
institutions that provide insurance products or services, provide
this option, and elect to use the model form may substitute the
word “policy” for “account” in this statement. Institutions that do
not provide this option may eliminate this left column from the
mail-in form.
(2) FCRA Section 603(d)(2)(A)(iii) opt-out. If the
institution shares personal information pursuant to section
603(d)(2)(A)(iii) of the FCRA, it must include in the mail-in
opt-out form the following statement: “□ Do not share information
about my creditworthiness with your affiliates for their everyday
business purposes.”
(3) FCRA Section 624 opt-out. If the institution
incorporates section 624 of the FCRA in accord with paragraph
C.2(d)(6) of these Instructions, it must include in the mail-in
opt-out form the following statement: “□ Do not allow your
affiliates to use my personal information to market to me.”
(4) Nonaffiliate opt-out. If the financial institution
shares personal information pursuant to § 248.10(a) of this part,
it must include in the mail-in opt-out form the following
statement: “□ Do not share my personal information with
nonaffiliates to market their products and services to me.”
(5) Additional opt-outs. Financial institutions that use
the disclosure table to provide opt-out options beyond those
required by Federal law must provide those opt-outs in this section
of the model form. A financial institution that chooses to offer an
opt-out for its own marketing in the mail-in opt-out form must
include one of the two following statements: “□ Do not share my
personal information to market to me.” or “□ Do not use my
personal information to market to me.” A financial institution that
chooses to offer an opt-out for joint marketing must include the
following statement: “□ Do not share my personal information with
other financial institutions to jointly market to me.”
(h) Barcodes. A financial institution may elect to
include a barcode and/or “tagline” (an internal identifier) in
6-point font at the bottom of page one, as needed for information
internal to the institution, so long as these do not interfere with
the clarity or text of the form.
3. Page Two
(a) General Instructions for the Questions. Certain of
the Questions may be customized as follows:
(1) “Who is providing this notice?” This question may be
omitted where only one financial institution provides the model
form and that institution is clearly identified in the title on
page one. Two or more financial institutions that jointly provide
the model form must use this question to identify themselves as
required by § 248.9(f) of this part. Where the list of institutions
exceeds four (4) lines, the institution must describe in the
response to this question the general types of institutions jointly
providing the notice and must separately identify those
institutions, in minimum 8-point font, directly following the
“Other important information” box, or, if that box is not included
in the institution's form, directly following the “Definitions.”
The list may appear in a multi-column format.
(2) “How does [name of financial institution] protect my
personal information?” The financial institution may only
provide additional information pertaining to its safeguards
practices following the designated response to this question. Such
information may include information about the institution's use of
cookies or other measures it uses to safeguard personal
information. Institutions are limited to a maximum of 30 additional
words.
(3) “How does [name of financial institution] collect my
personal information?” Institutions must use five (5) of the
following terms to complete the bulleted list for this question:
open an account; deposit money; pay your bills; apply for a loan;
use your credit or debit card; seek financial or tax advice; apply
for insurance; pay insurance premiums; file an insurance claim;
seek advice about your investments; buy securities from us; sell
securities to us; direct us to buy securities; direct us to sell
your securities; make deposits or withdrawals from your account;
enter into an investment advisory contract; give us your income
information; provide employment information; give us your
employment history; tell us about your investment or retirement
portfolio; tell us about your investment or retirement earnings;
apply for financing; apply for a lease; provide account
information; give us your contact information; pay us by check;
give us your wage statements; provide your mortgage information;
make a wire transfer; tell us who receives the money; tell us where
to send the money; show your government-issued ID; show your
driver's license; order a commodity futures or option trade.
Institutions that collect personal information from their
affiliates and/or credit bureaus must include after the bulleted
list the following statement: “We also collect your personal
information from others, such as credit bureaus, affiliates, or
other companies.” Institutions that do not collect personal
information from their affiliates or credit bureaus but do collect
information from other companies must include the following
statement instead: “We also collect your personal information from
other companies.” Only institutions that do not collect any
personal information from affiliates, credit bureaus, or other
companies can omit both statements.
(4) “Why can't I limit all sharing?” Institutions that
describe state privacy law provisions in the “Other important
information” box must use the bracketed sentence: “See below
for more on your rights under state law.” Other institutions must
omit this sentence.
(5) “What happens when I limit sharing for an account I hold
jointly with someone else?” Only financial institutions that
provide opt-out options must use this question. Other institutions
must omit this question. Institutions must choose one of the
following two statements to respond to this question: “Your choices
will apply to everyone on your account.” or “Your choices will
apply to everyone on your account - unless you tell us otherwise.”
Financial institutions that provide insurance products or services
and elect to use the model form may substitute the word “policy”
for “account” in these statements.
(b) General Instructions for the Definitions. The
financial institution must customize the space below the responses
to the three definitions in this section. This specific information
must be in italicized lettering to set off the information from the
standardized definitions.
(1) Affiliates. As required by § 248.6(a)(3) of this
part, where [affiliate information] appears, the financial
institution must:
(i) If it has no affiliates, state: “[name of financial
institution] has no affiliates;”
(ii) If it has affiliates but does not share personal
information, state: “[name of financial institution] does
not share with our affiliates;” or
(iii) If it shares with its affiliates, state, as applicable:
“Our affiliates include companies with a [common corporate
identity of financial institution] name; financial companies
such as [insert illustrative list of companies];
nonfinancial companies, such as [insert illustrative list of
companies] and others, such as [insert illustrative
list].”
(2) Nonaffiliates. As required by § 248.6(c)(3) of this
part, where [nonaffiliate information] appears, the
financial institution must:
(i) If it does not share with nonaffiliated third parties,
state: “[name of financial institution] does not share with
nonaffiliates so they can market to you;” or
(ii) If it shares with nonaffiliated third parties, state, as
applicable: “Nonaffiliates we share with can include [list
categories of companies such as mortgage companies, insurance
companies, direct marketing companies, and nonprofit
organizations].”
(3) Joint Marketing. As required by § 248.13 of this
part, where [joint marketing] appears, the financial
institution must:
(i) If it does not engage in joint marketing, state: “[name
of financial institution] doesn't jointly market;” or
(ii) If it shares personal information for joint marketing,
state, as applicable: “Our joint marketing partners include
[list categories of companies such as credit card
companies].”
(c) General instructions for the “Other important
information” box. This box is optional. The space provided for
information in this box is not limited. Only the following types of
information can appear in this box.
(1) State and/or international privacy law information;
and/or
(2) Acknowledgment of receipt form.
[74 FR 62985, Dec. 1, 2009]
Appendix A to Subpart C of Part 248 - Interagency Guidelines on Identity Theft Detection, Prevention, and Mitigation
17:4.0.1.1.9.3.128.3.3 : Appendix A
Appendix A to Subpart C of Part 248 - Interagency Guidelines on
Identity Theft Detection, Prevention, and Mitigation
Section 248.201 requires each financial institution and creditor
that offers or maintains one or more covered accounts, as defined
in § 248.201(b)(3), to develop and provide for the continued
administration of a written Program to detect, prevent, and
mitigate identity theft in connection with the opening of a covered
account or any existing covered account. These guidelines are
intended to assist financial institutions and creditors in the
formulation and maintenance of a Program that satisfies the
requirements of § 248.201.
I. The Program
In designing its Program, a financial institution or creditor
may incorporate, as appropriate, its existing policies, procedures,
and other arrangements that control reasonably foreseeable risks to
customers or to the safety and soundness of the financial
institution or creditor from identity theft.
II. Identifying Relevant Red Flags
(a) Risk Factors. A financial institution or creditor
should consider the following factors in identifying relevant Red
Flags for covered accounts, as appropriate:
(1) The types of covered accounts it offers or maintains;
(2) The methods it provides to open its covered accounts;
(3) The methods it provides to access its covered accounts;
and
(4) Its previous experiences with identity theft.
(b) Sources of Red Flags. Financial institutions and
creditors should incorporate relevant Red Flags from sources such
as:
(1) Incidents of identity theft that the financial institution
or creditor has experienced;
(2) Methods of identity theft that the financial institution or
creditor has identified that reflect changes in identity theft
risks; and
(3) Applicable regulatory guidance.
(c) Categories of Red Flags. The Program should include
relevant Red Flags from the following categories, as appropriate.
Examples of Red Flags from each of these categories are appended as
Supplement A to this Appendix A.
(1) Alerts, notifications, or other warnings received from
consumer reporting agencies or service providers, such as fraud
detection services;
(2) The presentation of suspicious documents;
(3) The presentation of suspicious personal identifying
information, such as a suspicious address change;
(4) The unusual use of, or other suspicious activity related to,
a covered account; and
(5) Notice from customers, victims of identity theft, law
enforcement authorities, or other persons regarding possible
identity theft in connection with covered accounts held by the
financial institution or creditor.
III. Detecting Red Flags
The Program's policies and procedures should address the
detection of Red Flags in connection with the opening of covered
accounts and existing covered accounts, such as by:
(a) Obtaining identifying information about, and verifying the
identity of, a person opening a covered account, for example, using
the policies and procedures regarding identification and
verification set forth in the Customer Identification Program rules
implementing 31 U.S.C. 5318(l) (31 CFR 1023.220
(broker-dealers) and 1024.220 (mutual funds)); and
(b) Authenticating customers, monitoring transactions, and
verifying the validity of change of address requests, in the case
of existing covered accounts.
IV. Preventing and Mitigating Identity Theft
The Program's policies and procedures should provide for
appropriate responses to the Red Flags the financial institution or
creditor has detected that are commensurate with the degree of risk
posed. In determining an appropriate response, a financial
institution or creditor should consider aggravating factors that
may heighten the risk of identity theft, such as a data security
incident that results in unauthorized access to a customer's
account records held by the financial institution, creditor, or
third party, or notice that a customer has provided information
related to a covered account held by the financial institution or
creditor to someone fraudulently claiming to represent the
financial institution or creditor or to a fraudulent Web site.
Appropriate responses may include the following:
(a) Monitoring a covered account for evidence of identity
theft;
(b) Contacting the customer;
(c) Changing any passwords, security codes, or other security
devices that permit access to a covered account;
(d) Reopening a covered account with a new account number;
(e) Not opening a new covered account;
(f) Closing an existing covered account;
(g) Not attempting to collect on a covered account or not
selling a covered account to a debt collector;
(h) Notifying law enforcement; or
(i) Determining that no response is warranted under the
particular circumstances.
V. Updating the Program
Financial institutions and creditors should update the Program
(including the Red Flags determined to be relevant) periodically,
to reflect changes in risks to customers or to the safety and
soundness of the financial institution or creditor from identity
theft, based on factors such as:
(a) The experiences of the financial institution or creditor
with identity theft;
(b) Changes in methods of identity theft;
(c) Changes in methods to detect, prevent, and mitigate identity
theft;
(d) Changes in the types of accounts that the financial
institution or creditor offers or maintains; and
(e) Changes in the business arrangements of the financial
institution or creditor, including mergers, acquisitions,
alliances, joint ventures, and service provider arrangements.
VI. Methods for Administering the Program
(a) Oversight of Program. Oversight by the board of
directors, an appropriate committee of the board, or a designated
employee at the level of senior management should include:
(1) Assigning specific responsibility for the Program's
implementation;
(2) Reviewing reports prepared by staff regarding compliance by
the financial institution or creditor with § 248.201; and
(3) Approving material changes to the Program as necessary to
address changing identity theft risks.
(b) Reports. (1) In general. Staff of the
financial institution or creditor responsible for development,
implementation, and administration of its Program should report to
the board of directors, an appropriate committee of the board, or a
designated employee at the level of senior management, at least
annually, on compliance by the financial institution or creditor
with § 248.201.
(2) Contents of report. The report should address
material matters related to the Program and evaluate issues such
as: The effectiveness of the policies and procedures of the
financial institution or creditor in addressing the risk of
identity theft in connection with the opening of covered accounts
and with respect to existing covered accounts; service provider
arrangements; significant incidents involving identity theft and
management's response; and recommendations for material changes to
the Program.
(c) Oversight of service provider arrangements. Whenever
a financial institution or creditor engages a service provider to
perform an activity in connection with one or more covered accounts
the financial institution or creditor should take steps to ensure
that the activity of the service provider is conducted in
accordance with reasonable policies and procedures designed to
detect, prevent, and mitigate the risk of identity theft. For
example, a financial institution or creditor could require the
service provider by contract to have policies and procedures to
detect relevant Red Flags that may arise in the performance of the
service provider's activities, and either report the Red Flags to
the financial institution or creditor, or to take appropriate steps
to prevent or mitigate identity theft.
VII. Other Applicable Legal Requirements
Financial institutions and creditors should be mindful of other
related legal requirements that may be applicable, such as:
(a) For financial institutions and creditors that are subject to
31 U.S.C. 5318(g), filing a Suspicious Activity Report in
accordance with applicable law and regulation;
(b) Implementing any requirements under 15 U.S.C. 1681c-1(h)
regarding the circumstances under which credit may be extended when
the financial institution or creditor detects a fraud or active
duty alert;
(c) Implementing any requirements for furnishers of information
to consumer reporting agencies under 15 U.S.C. 1681s-2, for
example, to correct or update inaccurate or incomplete information,
and to not report information that the furnisher has reasonable
cause to believe is inaccurate; and
(d) Complying with the prohibitions in 15 U.S.C. 1681m on the
sale, transfer, and placement for collection of certain debts
resulting from identity theft.
Supplement A to Appendix A
In addition to incorporating Red Flags from the sources
recommended in section II.b. of the Guidelines in Appendix A to
this subpart, each financial institution or creditor may consider
incorporating into its Program, whether singly or in combination,
Red Flags from the following illustrative examples in connection
with covered accounts:
Alerts, Notifications or Warnings From a Consumer Reporting Agency
1. A fraud or active duty alert is included with a consumer
report.
2. A consumer reporting agency provides a notice of credit
freeze in response to a request for a consumer report.
3. A consumer reporting agency provides a notice of address
discrepancy, as referenced in Sec. 605(h) of the Fair Credit
Reporting Act (15 U.S.C. 1681c(h)).
4. A consumer report indicates a pattern of activity that is
inconsistent with the history and usual pattern of activity of an
applicant or customer, such as:
a. A recent and significant increase in the volume of
inquiries;
b. An unusual number of recently established credit
relationships;
c. A material change in the use of credit, especially with
respect to recently established credit relationships; or
d. An account that was closed for cause or identified for abuse
of account privileges by a financial institution or creditor.
Suspicious Documents
5. Documents provided for identification appear to have been
altered or forged.
6. The photograph or physical description on the identification
is not consistent with the appearance of the applicant or customer
presenting the identification.
7. Other information on the identification is not consistent
with information provided by the person opening a new covered
account or customer presenting the identification.
8. Other information on the identification is not consistent
with readily accessible information that is on file with the
financial institution or creditor, such as a signature card or a
recent check.
9. An application appears to have been altered or forged, or
gives the appearance of having been destroyed and reassembled.
Suspicious Personal Identifying Information
10. Personal identifying information provided is inconsistent
when compared against external information sources used by the
financial institution or creditor. For example:
a. The address does not match any address in the consumer
report; or
b. The Social Security Number (SSN) has not been issued, or is
listed on the Social Security Administration's Death Master
File.
11. Personal identifying information provided by the customer is
not consistent with other personal identifying information provided
by the customer. For example, there is a lack of correlation
between the SSN range and date of birth.
12. Personal identifying information provided is associated with
known fraudulent activity as indicated by internal or third-party
sources used by the financial institution or creditor. For
example:
a. The address on an application is the same as the address
provided on a fraudulent application; or
b. The phone number on an application is the same as the number
provided on a fraudulent application.
13. Personal identifying information provided is of a type
commonly associated with fraudulent activity as indicated by
internal or third-party sources used by the financial institution
or creditor. For example:
a. The address on an application is fictitious, a mail drop, or
a prison; or
b. The phone number is invalid, or is associated with a pager or
answering service.
14. The SSN provided is the same as that submitted by other
persons opening an account or other customers.
15. The address or telephone number provided is the same as or
similar to the address or telephone number submitted by an
unusually large number of other persons opening accounts or by
other customers.
16. The person opening the covered account or the customer fails
to provide all required personal identifying information on an
application or in response to notification that the application is
incomplete.
17. Personal identifying information provided is not consistent
with personal identifying information that is on file with the
financial institution or creditor.
18. For financial institutions and creditors that use challenge
questions, the person opening the covered account or the customer
cannot provide authenticating information beyond that which
generally would be available from a wallet or consumer report.
Unusual Use of, or Suspicious Activity Related to, the Covered
Account
19. Shortly following the notice of a change of address for a
covered account, the institution or creditor receives a request for
a new, additional, or replacement means of accessing the account or
for the addition of an authorized user on the account.
20. A covered account is used in a manner that is not consistent
with established patterns of activity on the account. There is, for
example:
a. Nonpayment when there is no history of late or missed
payments;
b. A material increase in the use of available credit;
c. A material change in purchasing or spending patterns; or
d. A material change in electronic fund transfer patterns in
connection with a deposit account.
21. A covered account that has been inactive for a reasonably
lengthy period of time is used (taking into consideration the type
of account, the expected pattern of usage and other relevant
factors).
22. Mail sent to the customer is returned repeatedly as
undeliverable although transactions continue to be conducted in
connection with the customer's covered account.
23. The financial institution or creditor is notified that the
customer is not receiving paper account statements.
24. The financial institution or creditor is notified of
unauthorized charges or transactions in connection with a
customer's covered account.
Notice From Customers, Victims of Identity Theft, Law Enforcement
Authorities, or Other Persons Regarding Possible Identity Theft in
Connection With Covered Accounts Held by the Financial Institution
or Creditor
25. The financial institution or creditor is notified by a
customer, a victim of identity theft, a law enforcement authority,
or any other person that it has opened a fraudulent account for a
person engaged in identity theft.